TCPWave's DNS Titan End-User Security prevents users from accessing malicious sites. More specifically, it blocks DNS queries for domain names of malicious hosts, queries
to malicious DNS servers, and IP addresses of malicious sites in DNS query responses. Also, since this Titan feature provides this protection in DNS servers, it prevents some types of malware from reaching devices. Consequently, there is not a need
to attempt to quickly detect this malware on a device and remove it before it does damage or spreads.
Additionally, although the emphasis here is on protecting end users, this Titan feature protects all DNS clients, including applications that make DNS queries. Furthermore, it provides this protection without having to install and continually update software on the many DNS clients that exist.
The items to block are based on domain and IP reputation data provided by TCPWave's partner, Spamhaus, a leader in providing high-quality threat intelligence information. This reputation data consists of a feed of continually updated rules in DNS Response Policy Zones (RPZs). By using this information, Titan End-User Security protects users from accessing malicious
sites, including malware, ransomware, phishing, adware, and botnet sites.
Additional information on DNS Titan End-User Security, including sections on Spamhaus and the Titan architecture, is presented below.
Spamhaus has over twenty years of experience protecting users and networks and is a trusted authority on IP and domain reputation data. Also, they protect over three billion mailboxes globally. Consequently, they are an industry leader for providing threat intelligence data, and their datasets are used by leading global technology companies.
Example customers are provided near the bottom of the page at www.spamhaus.com.
With DNS Titan End-User Security, you benefit from Spamhaus's high-quality threat intelligence in their RPZ data feeds. The following data feeds from Spamhaus are included in DNS Titan End-User Security:
-
Malware Hosts: Domains identified as hosting malware.
-
Phishing Hosts: Domains identified as hosting phishing sites.
-
Adware Hosts: Domains identified as hosting adware.
-
Bad Reputation Hosts: Uncategorized domains that have a bad reputation. This includes hosts owned by known spammers, payload URLs, malicious tracking domains, and domains associated with low reputation networks, among others.
-
Botnet Command and Control (C&C) Hosts: Domains identified as hosting botnet C&C malware.
-
Botnet Hosts: Domains identified as hosting botnet resources that are not a botnet C&C.
-
Domain Generation Algorithm: Domains produced by domain generation algorithms. These domains are usually associated with malware.
-
Zero Reputation Domains: Newly registered domains that have been listed for less than 24 hours. Legitimate organizations rarely use a domain immediately after registering it.
-
Bad Nameserver Hosts: Domains used for the host records of nameservers that have a bad reputation.
-
Bad Nameserver IPs: IP addresses of nameservers that host domains and have a bad reputation.
-
Botnet Command and Control (C&C) IPs: IP addresses identified as hosting botnet C&C malware.
-
Bogons IPs: IP addresses that have not yet been assigned to an entity, so should not have any incoming or outgoing traffic.
-
Do Not Route or Peer: IP addresses that have been identified as being hijacked, belonging to bulletproof hosters, or being leased by professional malicious organizations.
-
Coinblocker: IP addresses and domains that host cryptojacking scripts, which use the resources of an end user's computer to mine cryptocurrency.
-
Torblocker: List of known Tor Exit Nodes.
An overview of the DNS Titan End-User Security architecture is shown in the figure below. As depicted in it, Response Policy Zones (RPZs) are transferred from Spamhaus DNS servers to a TCPWave primary (or lead secondary) DNS caching appliance. Spamhaus also supports transfers to an optional primary DNS appliance, for site and geographic redundancy. Secondary DNS caching
appliances are downstream from the primary DNS appliances and get zone transfers from them.
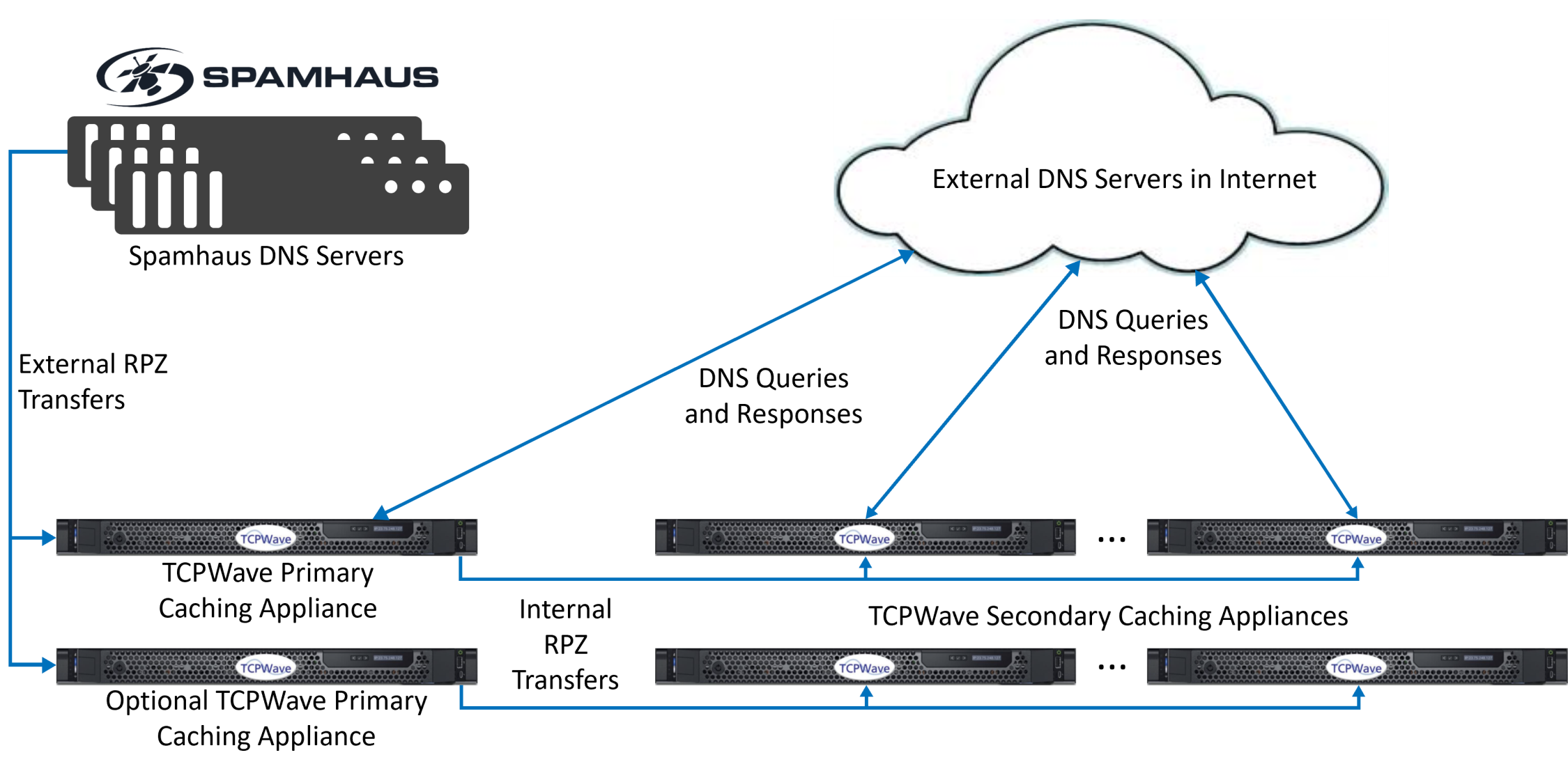
DNS Titan End-User Security Architecture
After zone transfers complete, if a DNS query contains a name or IP address that is defined in an RPZ as being
malicious, the query will be blocked. Also, these blocked queries will be logged and used in DNS RPZ reports.
The content above and additional sections, including ones on configuring the Titan feature, verifying the configuration, and reports for this feature, are available in a complete document. You can access it by using the download button below.







