Active Directory is a directory service developed by Microsoft
that stores objects such as users, computers, printers, and network
information. It is primarily used for authentication and resource
management within an Active Directory domain, and it relies heavily
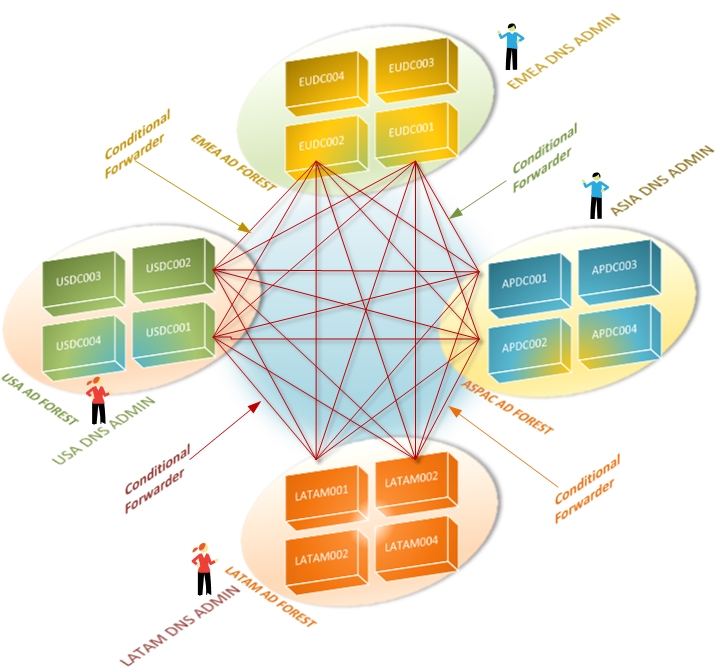
on the DNS infrastructure. One-to-one mapping between an AD forest
name and a DNS domain name is mandatory, and domain controllers
self-register their DNS resource records. While it is a common
misconception that Microsoft's AD requires Microsoft's DNS, TCPWave's
DDI management seamlessly integrates with Microsoft Active Directory
and provides numerous advantages.
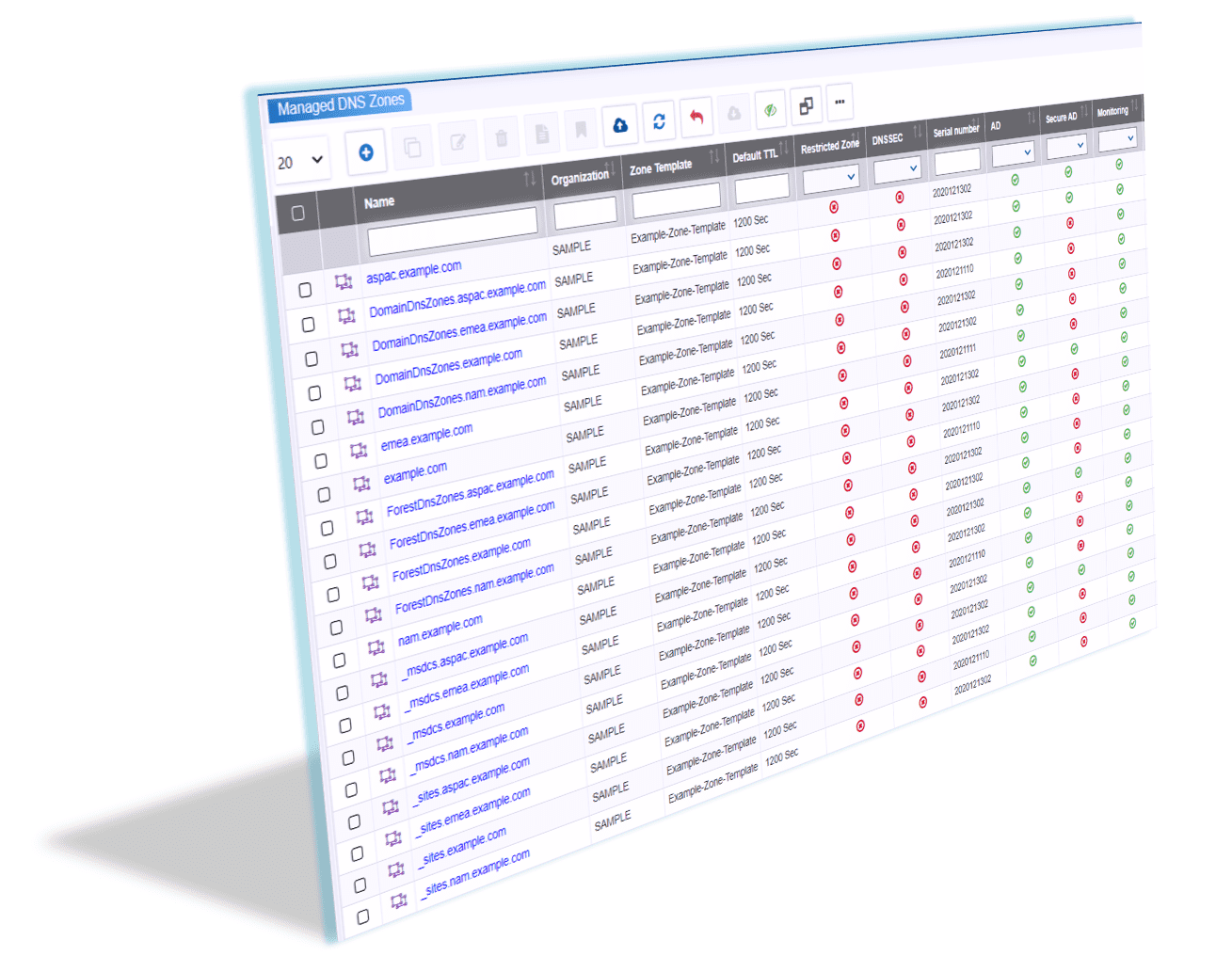
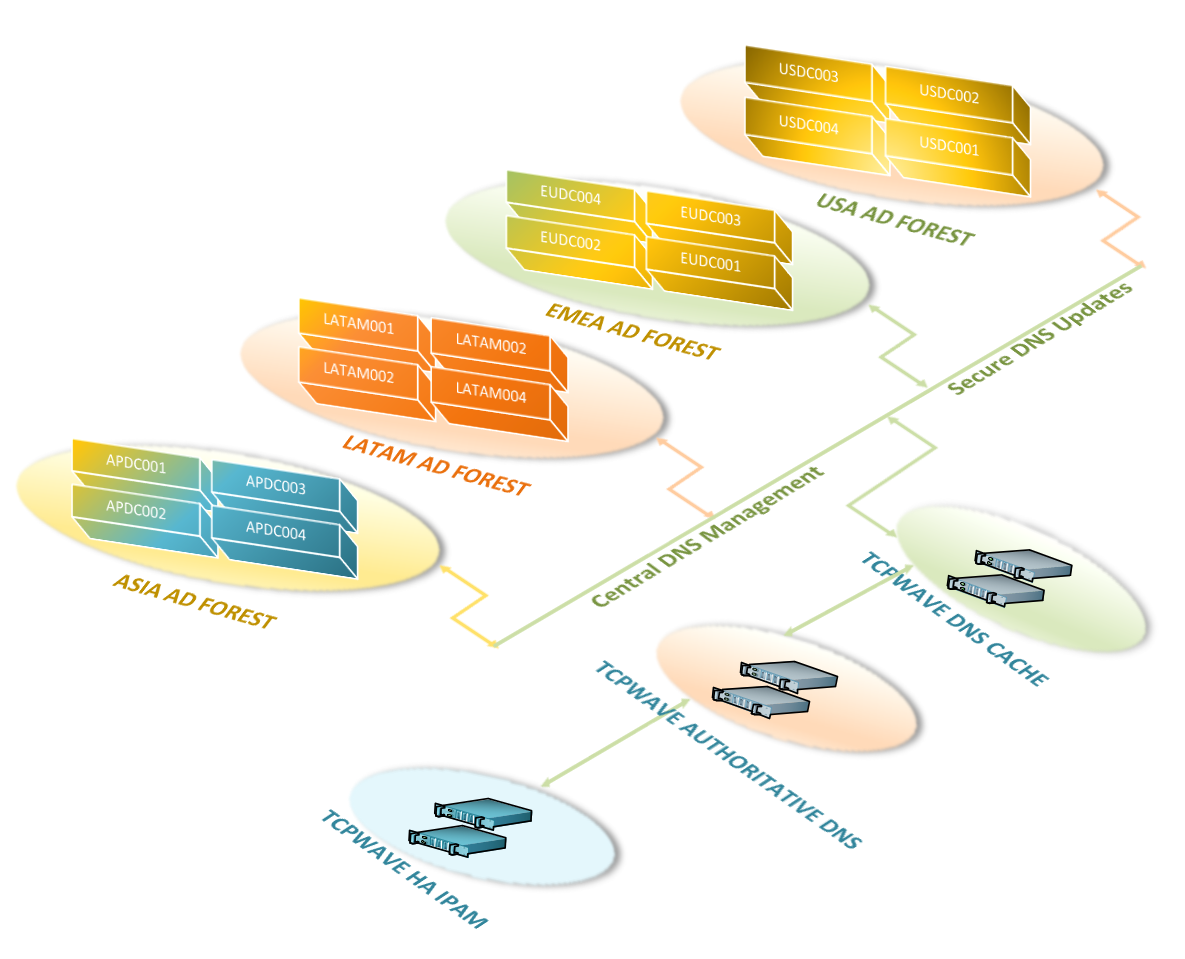
Our DDI solution centralizes DNS management in the
organization and manages large AD environments with ease. It adds
stability by centralizing DDI management and provides auditing,
reporting, disaster recovery, monitoring, role-based access control,
and many more features. Our IPAM runs in a high availability
mode and manages authoritative and cache DNS appliances. Each domain
controller in each AD forest updates the authoritative DNS zone
hosted on the authoritative DDI remote. Our design
provides seamless AD integration with simplified management of
Kerberos configurations, Service Principal Names (SPN), secure DNS
update policies, TSIG keys, and more, across all AD-enabled DNS
zones.