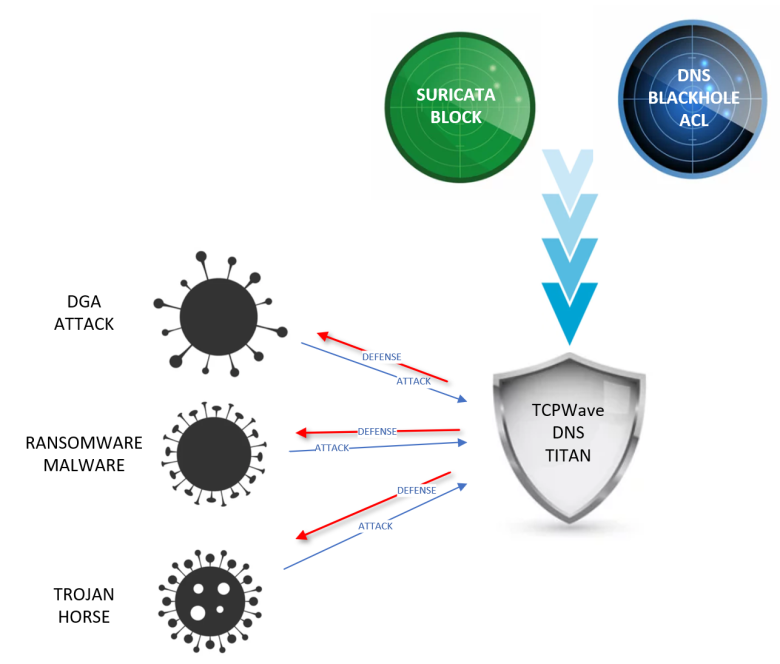
DNS security is one of the critical components of network security infrastructure that is an everlasting field of turmoil and sweating. Defense mechanisms are shattered, and counterattacks are planned frequently. Hence the networks tend to be vulnerable due to the malicious traffic. It requires a nip in the bud mechanism. One such option to restrict the malicious traffic flow is the usage of Access Control Lists (ACLs). This whitepaper provides insights on auto-blocking malicious traffic using DNS Blackhole ACL mechanism in the TCPWave IPAM application.
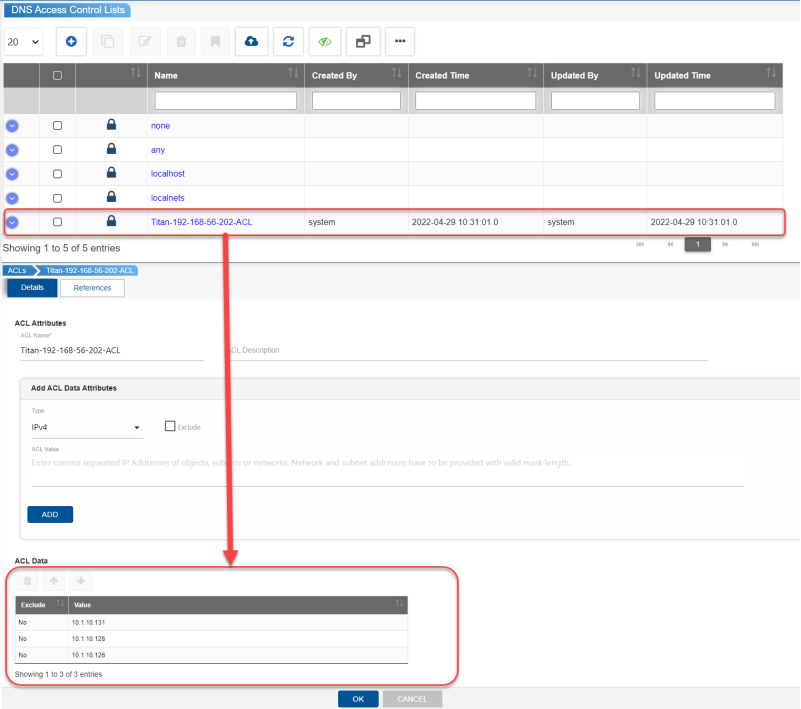
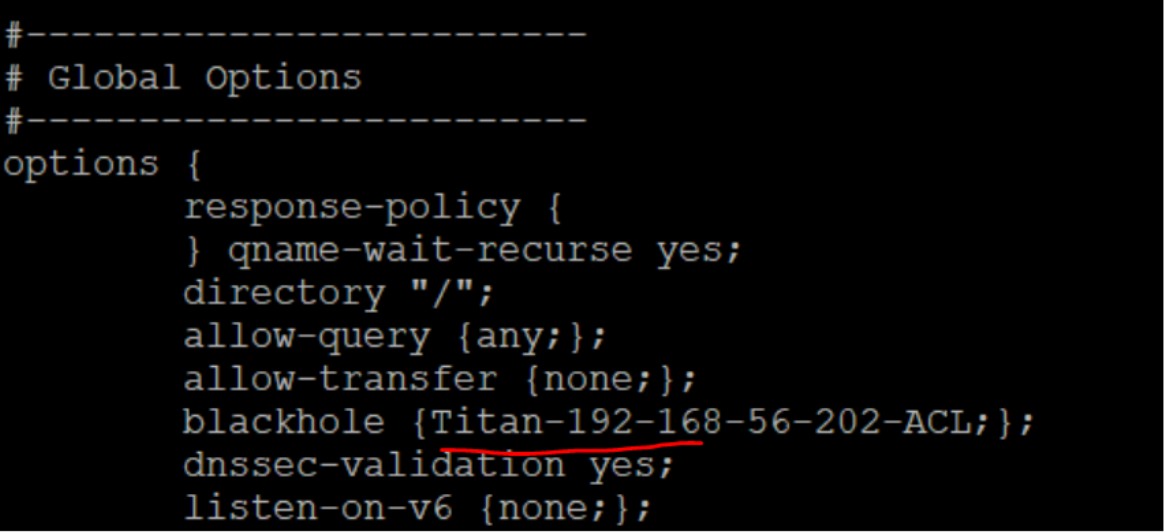
The DNS Blackhole ACL feature provides the ability to specify the IP address of a client that you do not want to use in the DNS resolution process. The ACL is auto-created when the anomaly detection alerts the TCPWave IPAM application. The recursive cache blocks the source IP at layer 7 or the application layer. On the other hand, Suricata filters at layer 4 or transport layer.
In the TCPWave IPAM application, if a source IP is declared as malicious by our Network Security Monitoring (NSM) platform, then it is added to blackhole option section of the DNS appliance configuration. The architecture is shown as below:

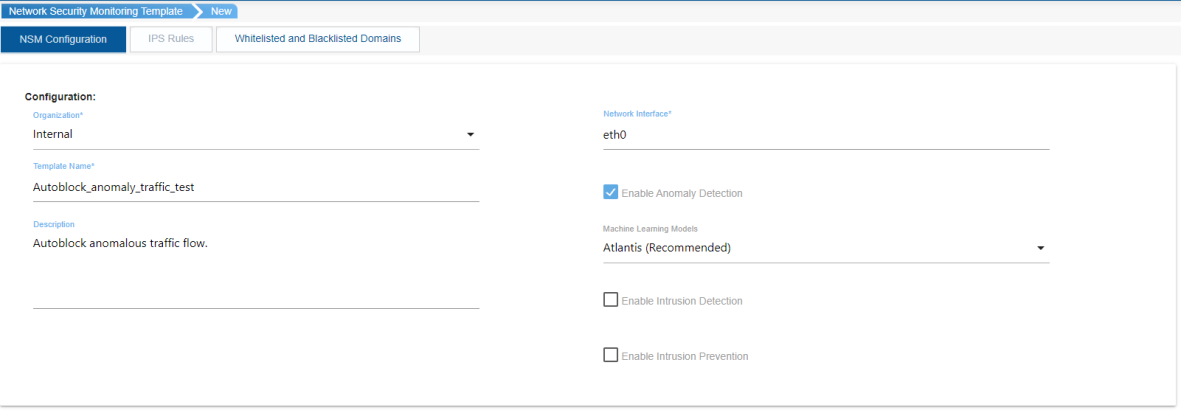
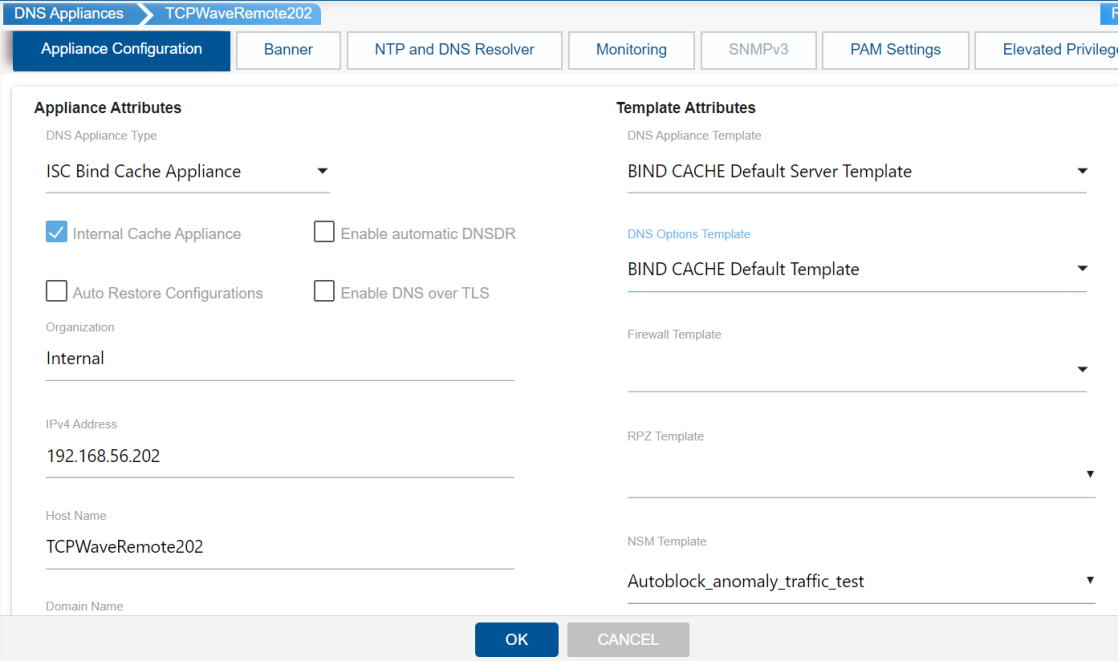
The process to automatically block anomalous traffic by using DNS Blackhole ACL option is as follows:
To initiate the anomaly detection process on the DNS remote appliance:
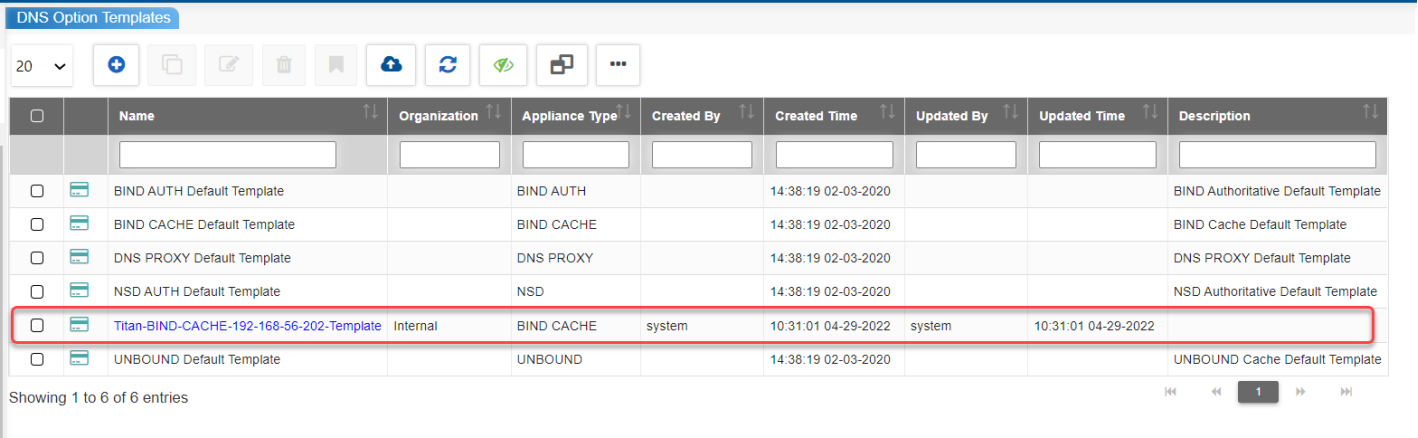
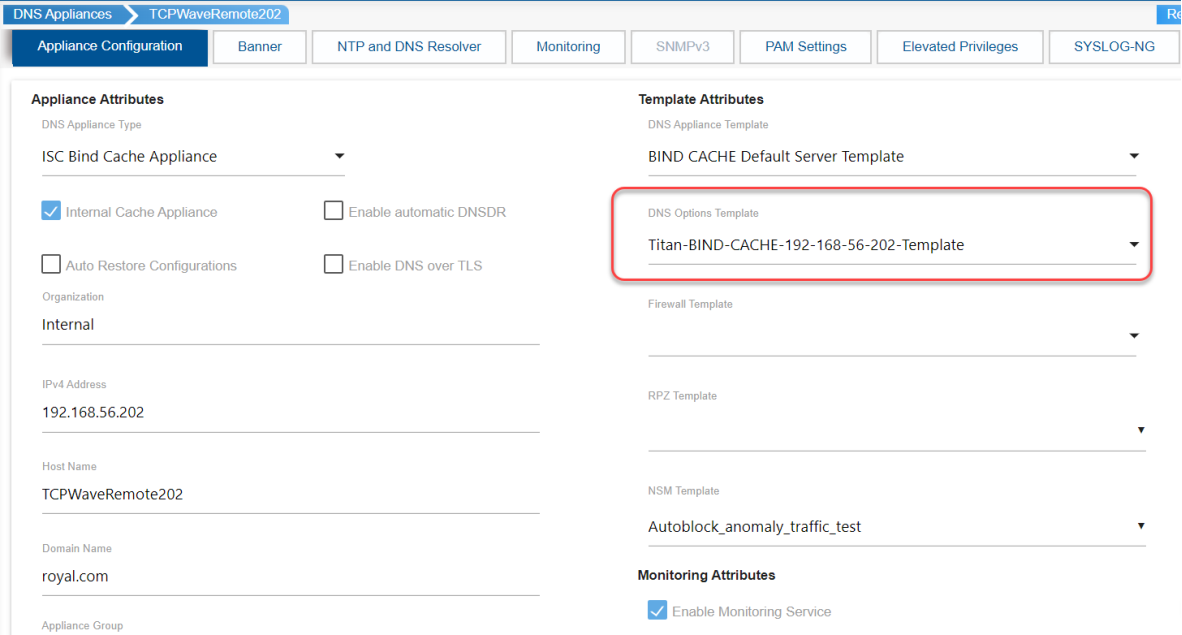
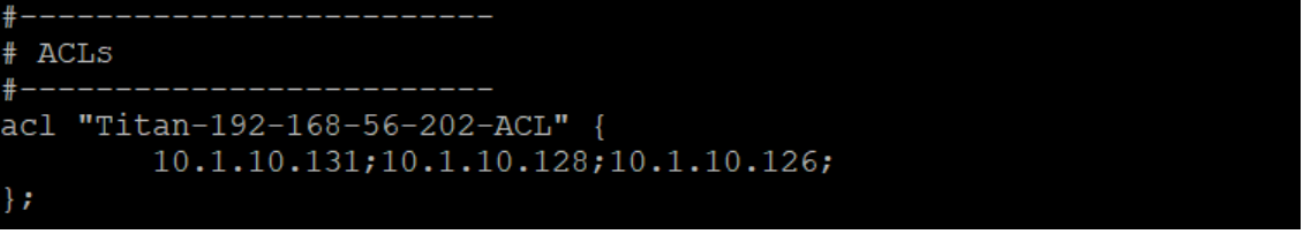
The audit management help the organizations to gain visibility, identify the security risks by uncovering the underlying network issues, thereby improving the overall network architecture. The operations of ACL, DNS Option Template and DNS appliance performed internally by system user as part of autoblock anomalous traffic functionality is audited. These operations can be viewed at Reports >> Change Reconciliation >> Adhoc Audit Report as shown:
|
Description |
Screenshot |
|
Adhoc Audit Report |
|
|
Auto-created ACL |
|
|
Auto-created DNS Option Template |
|
|
|
|
With TCPWave’s Infrastructure Management, organizations can avail monitoring activities in real-time and fetch predictive analytics to detect the issues.
The alerts are generated in Fault Management >> Current Alarms section for all the operations that are performed while configuring ACLs, DNS Option Template, NSM Template, DNS Appliance, as part of autoblock anomalous traffic functionality. The system generates OK alerts when the auto-block operation is successful and generates critical alert when the auto-block operation fails. The network administrators needs to view the logs to take an appropriate action in fixing the issue related to critical alert.
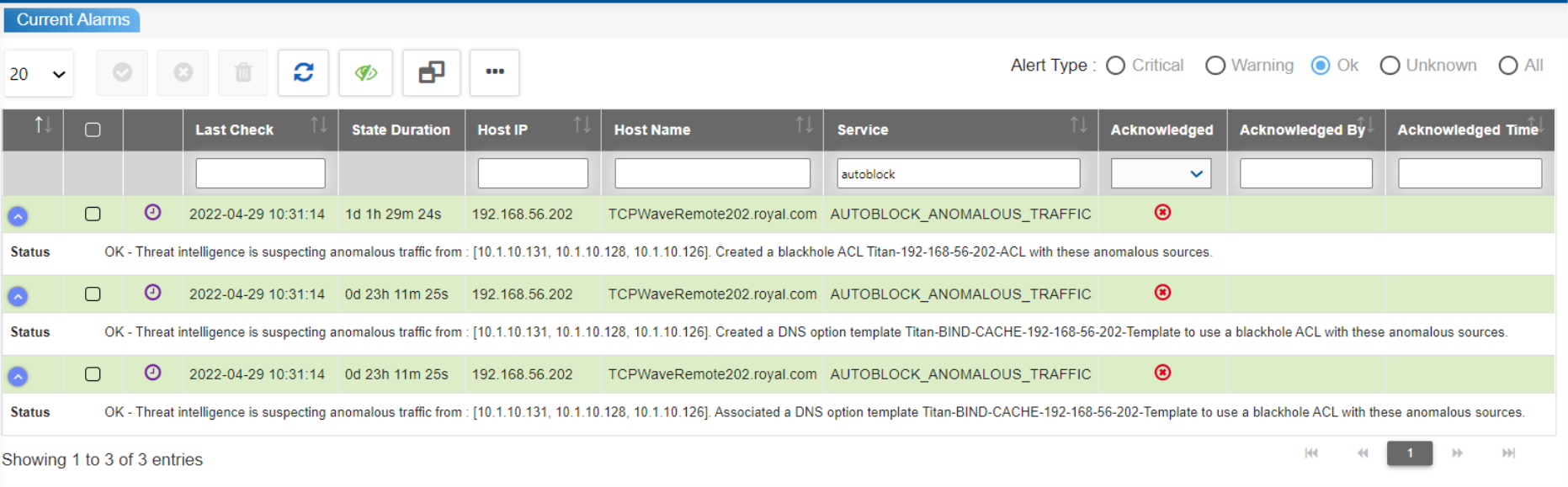
The TCPWave’s comprehensive security solutions effectively shield the organizations from the widest range of attacks, uncovers attacker infrastructure there by improving security stack, efficiency, productivity, maintaining service uptime for your organization. For a demo, contact the TCPWave Sales Team