As the years went by, user authentication and permission settings have been critical aspects of computer systems. Ever since MIT used a username and password to authenticate users, it remained part of the user interactions with the procedures and applications. After several decades later, to ensure system security, several methods have been used to authenticate users. For an organization, several types of users access the systems and applications, especially the internal ones. Several applications require logins with user accounts, sometimes the same account but with different user permissions.
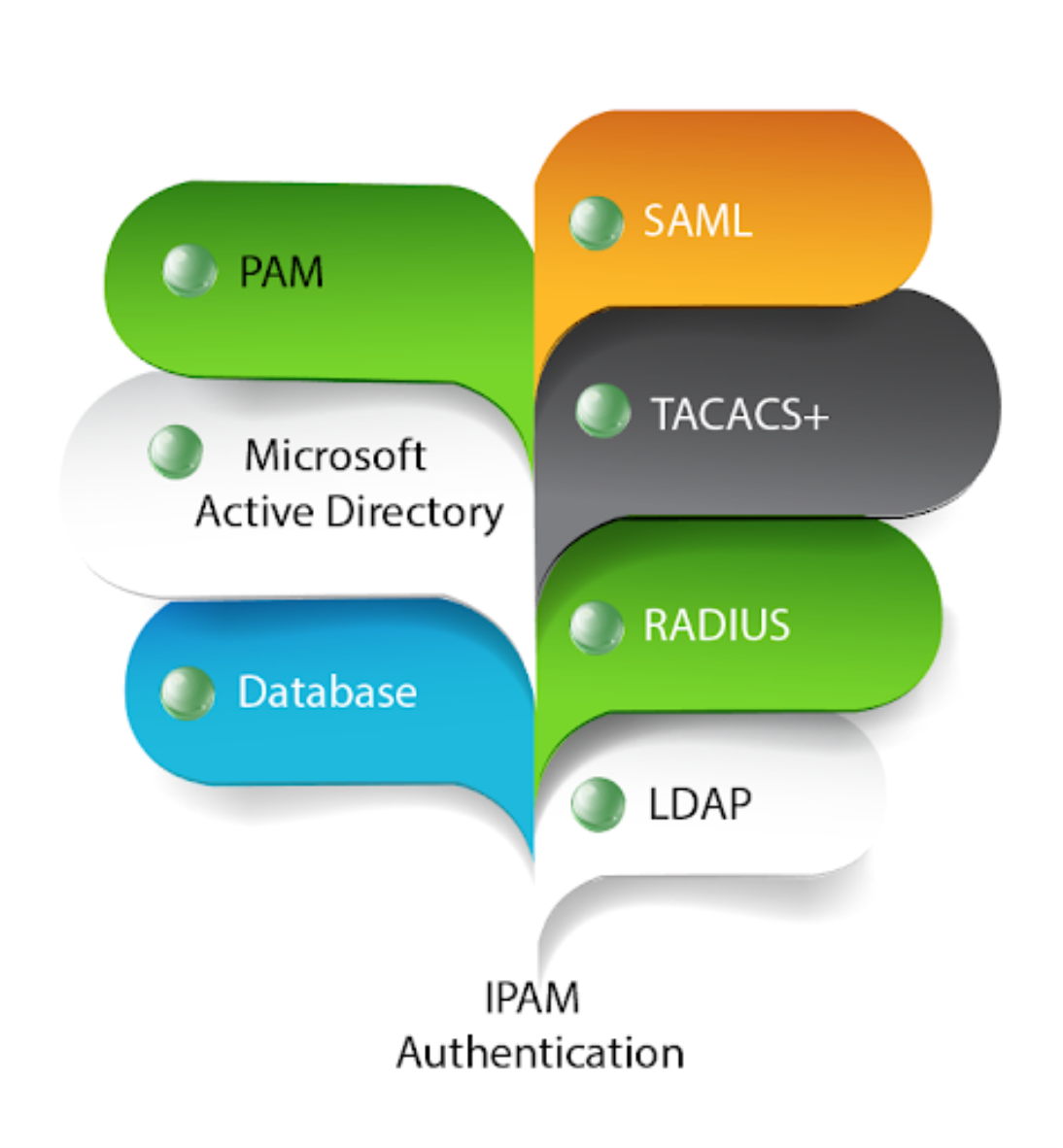
TCPWave supports the following user authentication methods:

This whitepaper outlines the user authentication configuration in IPAM using LDAP.
A Lightweight Directory Access Protocol (LDAP) server is a lightweight implementation of the Directory Access Protocol (DAP). As originally intended, X.500 Directory Low-Overhead Access provided low-overhead access to X.500 Directory. One of LDAP's main functions is to provide quick and easy access to information about organizations, people, and more. The LDAP directory stores data and authenticates users to achieve this goal. In addition to providing applications with a means of interacting with directory services, it also provides a standard language for exchanging information.
You can find data and resources through LDAP including files and user information. It collaborates with printers, computers, and other devices connected to the internet or a company's intranet. Most vendor directory services, such as Active Directory (AD), support LDAP. It becomes easier to share information about users, services, systems, networks, and applications from a directory service to other applications and services with LDAP.
LDAP database or directory information is a TCP protocol, that is leveraged for user authentication. LDAP databases can be replicated across multiple LDAP servers. The authentication uses port 389/tcp for normal LDAP and port 636/tcp for secure LDAP. The LDAP database contains information about users, groups, and permissions and delivers this data to connected applications. The client-server verifies Users and passwords by connecting to an LDAP directory service to validate their credentials. OpenLDAP, MS Active Directory, and OpenDJ are among the LDAP directory servers.
The following explains the authentication process:
It's worth noting that the core user identity saved in the LDAP database includes more than just usernames and passwords, including addresses, phone numbers, and group associations.
TCPWave fully supports LDAP authentication and works with different directory service providers, predominantly Microsoft Active Directory.
The following are the required prerequisites to be followed by the users while setting the IPAM LDAP integration:
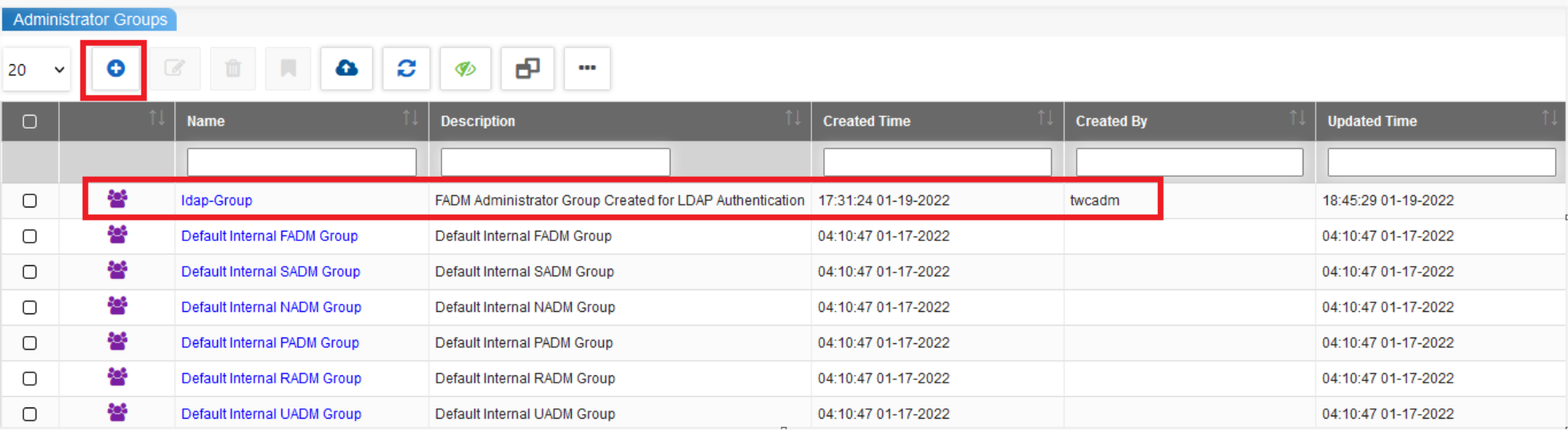
Create an Administrator group for LDAP authentication. Please give it a name and assign a Role like FADM, PADM, NADM, etc. For this, please navigate to Administration -> Security Management -> Administrator Groups -> Add a new group using the ‘+’ icon. In the below screenshot you can see such a group was created with the name LDAP-Group.
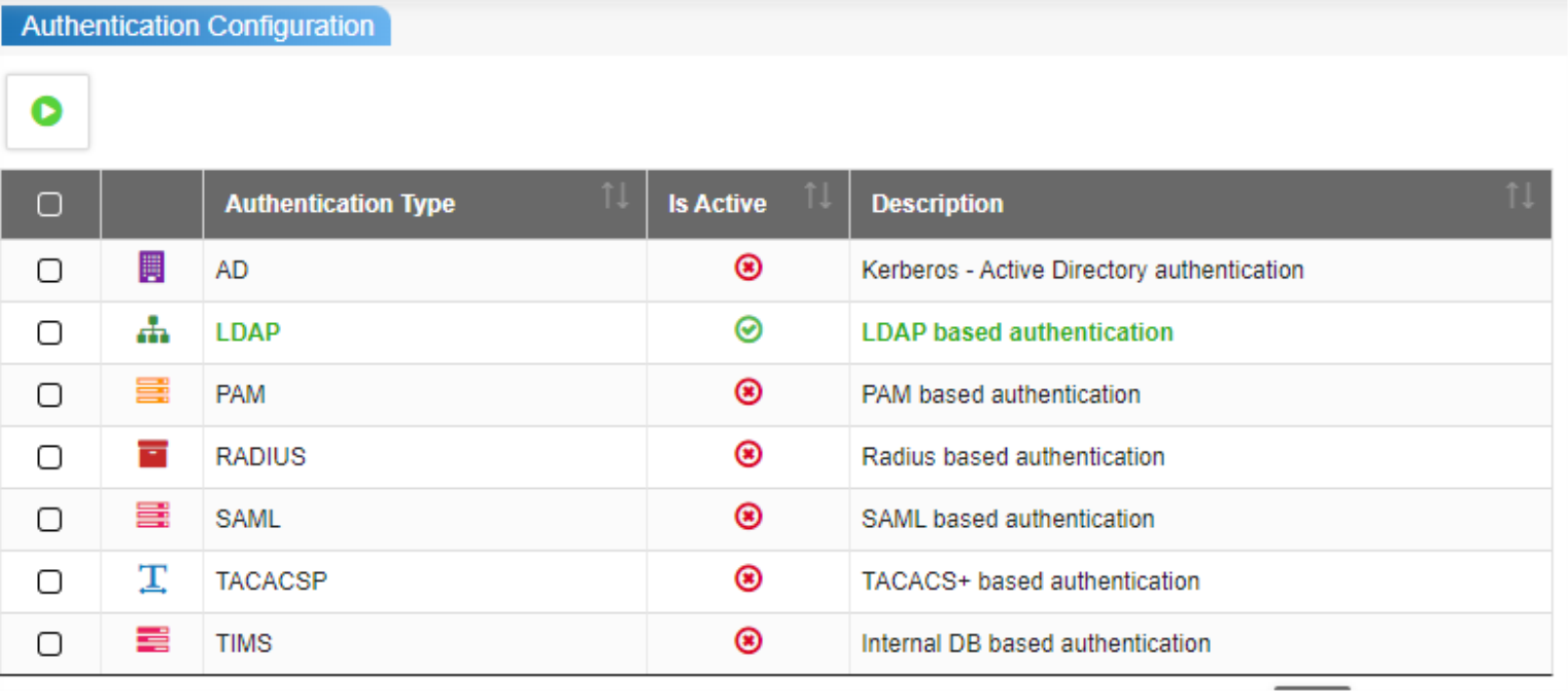
To enable the LDAP authentication, navigate to Administration >> Security Management >> Authentication Configuration, start the LDAP authentication Type, as shown in the image below.
First, select the LDAP authentication type using the check box on the left and click ![]() .
.
Once this is done, you can log in to the IPAM with the LDAP user credentials successfully.
To Import users to IPAM, the global options for LDAP should be entered in Configuration >> Global Policy Management. In IPAM, navigate to Administration >> Security Management >> AD/LDAP Admins, you will find the top section of AD/LDAP configuration is preloaded, but it doesn’t allow editing on this page.
However, in LDAP global policy management, if the option “LDAP Automatic IPAM User creation” is set to Yes, and if the person logs in and belongs to the group that has been authorized, then the users will get automatically created in the IPAM in case the user group already exists in TCPWave IPAM. On the other hand, if the user is previously enabled and later disabled in LDAP, if the global policy option “LDAP Automatic IPAM User Deletion” is set to yes, the user will get automatically deleted from TCPWave IPAM.
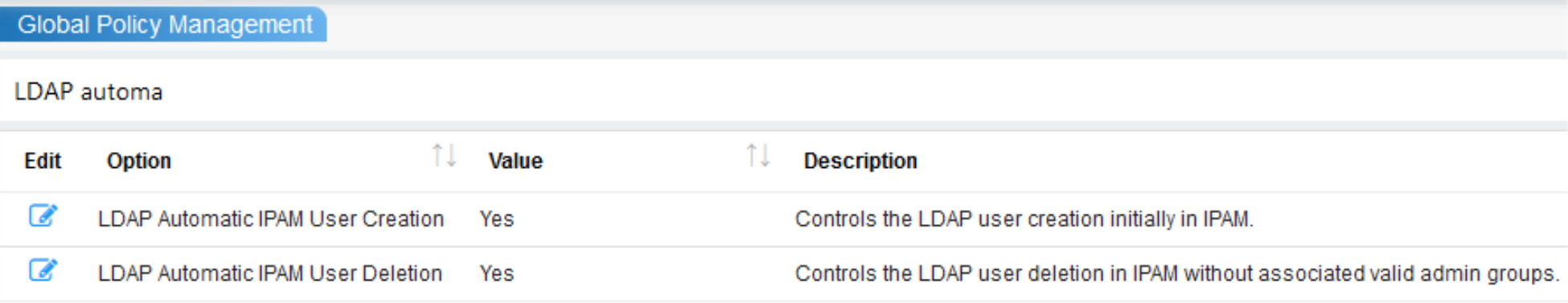
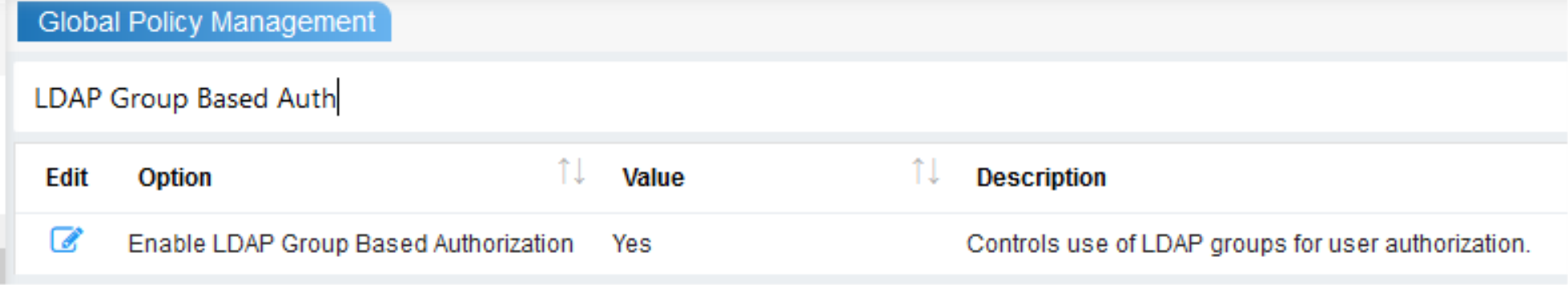
For LDAP Group Based Authorization to work, the following should be done.
How does this option work?
The administrator needs to define the global security settings for LDAP under global policy Management. The following needs to be determined.
Note:
TCPWave DDI solution assists our customers to manage and modernize their enterprise-grade solutions by ensuring they have the most innovative technology with minimal risks. For a quick demo, contact the TCPWave Sales Team.